WebRTC Leak Prevent Example
In this post, we will discuss what WebRTC Leak is and how to mitigate the risks posed by it. WebRTC is a set of APIs that allow peer to peer connections without the need of a relaying server in between. Without an intermediary in between, this connection allows real-time communications between the peers. Since the concern was raised about leak of private IP addresses through WebRTC, browser vendors have come up with solutions to prevent it and put the user in charge of matters. We will be exploring such solutions and the impact that they have on WebRTC features.
1. Identifying a Leak
We will start with trying to understand the nature of the problem and the solutions we can apply to resolve the issues. To establish a connection, details like the private/public IP addresses of the machines are exchanged. The STUN servers expose the IP address when it receives a UDP packet from a client, returning the details of the address from which the request originated. If this is abused, a website may use WebRTC to establish a peer connection and get access to details including Public/Private IP Addresses, even if you are connected via VPN. This is in essence what is meant by a WebRTC Leak. The user themselves are not aware, much less agree to, share such information with a website. Browser vendors have come up with extensions that change settings to give the user control over this.
Some solutions involve completely disabling WebRTC altogether to controlling the addresses shared through WebRTC APIs. In the below sections we will explore such extensions for various browsers.
To identify whether you are affected by this, you can visit one of the below sites, to know what details are being exposed via WebRTC.
- https://browserleaks.com/webrtc
- https://diafygi.github.io/webrtc-ips/
- https://www.perfect-privacy.com/webrtc-leaktest/
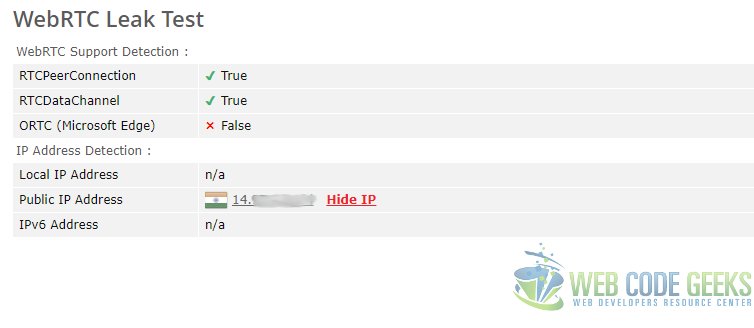
You will see the below screen that will show you what information can be collected using WebRTC feature.
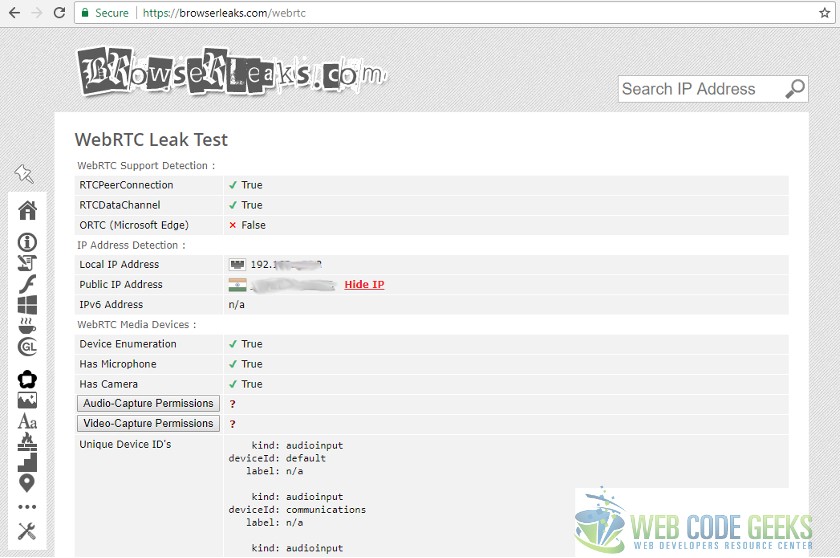
You will note that the smudged out IP Addresses include the Public IP as well. In the following sections we will take a look at the effects that the use of extensions has as well as changing browser settings on the information leaked.
2. Google Chrome Solutions
The Google Chrome browser supports WebRTC since version 23. Chrome was one of the browsers to support WebRTC from early on. Following extensions are available for the Chrome browser to limit or control the leak of IP Address through WebRTC feature. Let us take a look at each of these extensions.
First up is the Network limiter extension available through Chrome Web Store. Just search for WebRTC Network Limiter and you should see the below extension, just add it to chrome.

This extension has options to configure settings for the WebRTC features in chrome. The available options are as below:
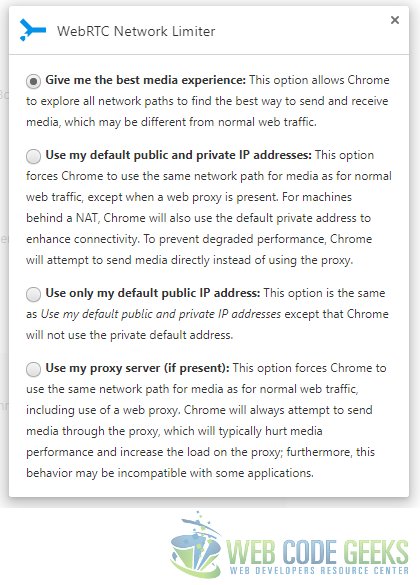
As you can see in the screen capture above that the extension provides us four options. Below are the details exposed when each of those options is selected.
- Give me the best media experience
After selecting this option, the information on the Browser Leaks website looks as follows:

- Use my default public and private IP Addresses
- Use only my default public IP Address
- Use my proxy server (if present)
As you can see from the above, this extension from Google for Chrome puts the user in control of the information that is shared. Although limiting the information shared might degrade the performance of the WebRTC feature because only a subset of routes between peers are possible with limitations on sharing information.
3. Firefox Solution
The Firefox browser supports WebRTC feature since version 22, that is enabled by default. Let us take a look at the solution for the Firefox browser to fix the leak issue. To start off, open an instance of the Firefox browser and enter this as the URL: about:config
You will be asked to confirm if you are going to be careful while editing the settings. Confirm it and once you do you will see the below list of settings.
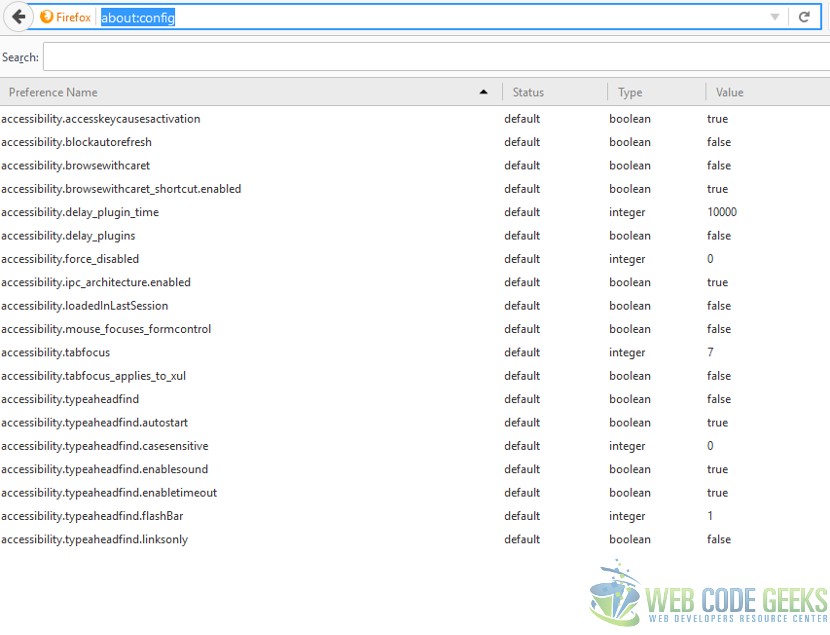
Search for the following settings by entering the following in the search bar: media.peerconnection.enabled
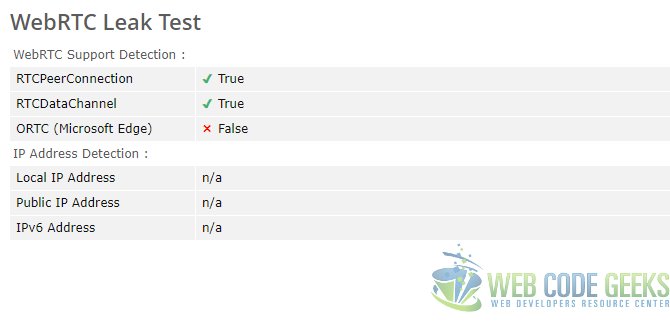
Set this to false by double-clicking the setting and then close the tab. Navigate to the BrowserLeaks URL to check the effect of this setting. You should see the below:
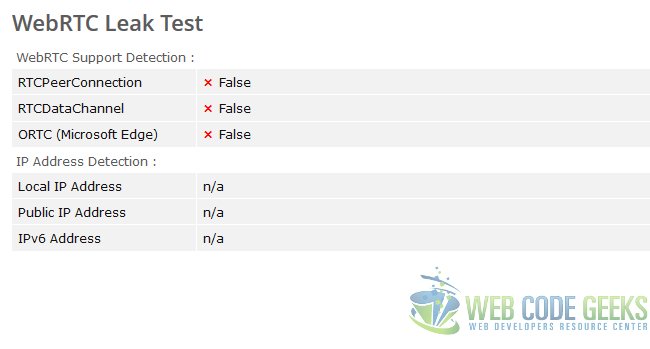
As you can see this change completely blocked out sensitive details.
4. Summary
To summarize, we learnt what a WebRTC Leak is and how we can safeguard against such a leak. We then looked for solutions for each of the two major browsers that support WebRTC feature natively.